CyberArk Conjur¶
HPE Morpheus Enterprise supports integration with CyberArk Conjur for stored credential sets as well utilization of Conjur-stored secret values via HPE Morpheus Enterprise Cypher service. This works identically to built-in credential storage and built-in Cypher functionality with the exception that your Conjur server is the storage backend rather than the HPE Morpheus Enterprise appliance itself. In some cases, this may help to consolidate secret management into one central place or it even may be a requirement to satisfy internal security policies at some organizations.
CyberArk Conjur integration is not included with HPE Morpheus Enterprise out of the box. It is developed as an official plugin and may be applied to any HPE Morpheus Enterprise appliance that needs it. See the HPE Morpheus Enterprise plugin repository website for access to the latest version of the plugin.
Applying the Plugin¶
The latest version of the CyberArk Conjur plugin is available at the HPE Morpheus Enterprise plugin share site. Select the pane for the correct plugin and click the DOWNLOAD button. The plugin JAR file will be downloaded to the local computer you’re working on.

With the plugin downloaded, head back to HPE Morpheus Enterprise to apply the plugin to your appliance. Plugins are added by navigating to Administration > Integrations > Plugins and clicking ADD. Drop the plugin JAR file onto the target and click UPLOAD. It may take a few moments for the plugin to be applied successfully and for the modal to be dismissed after clicking the upload button.
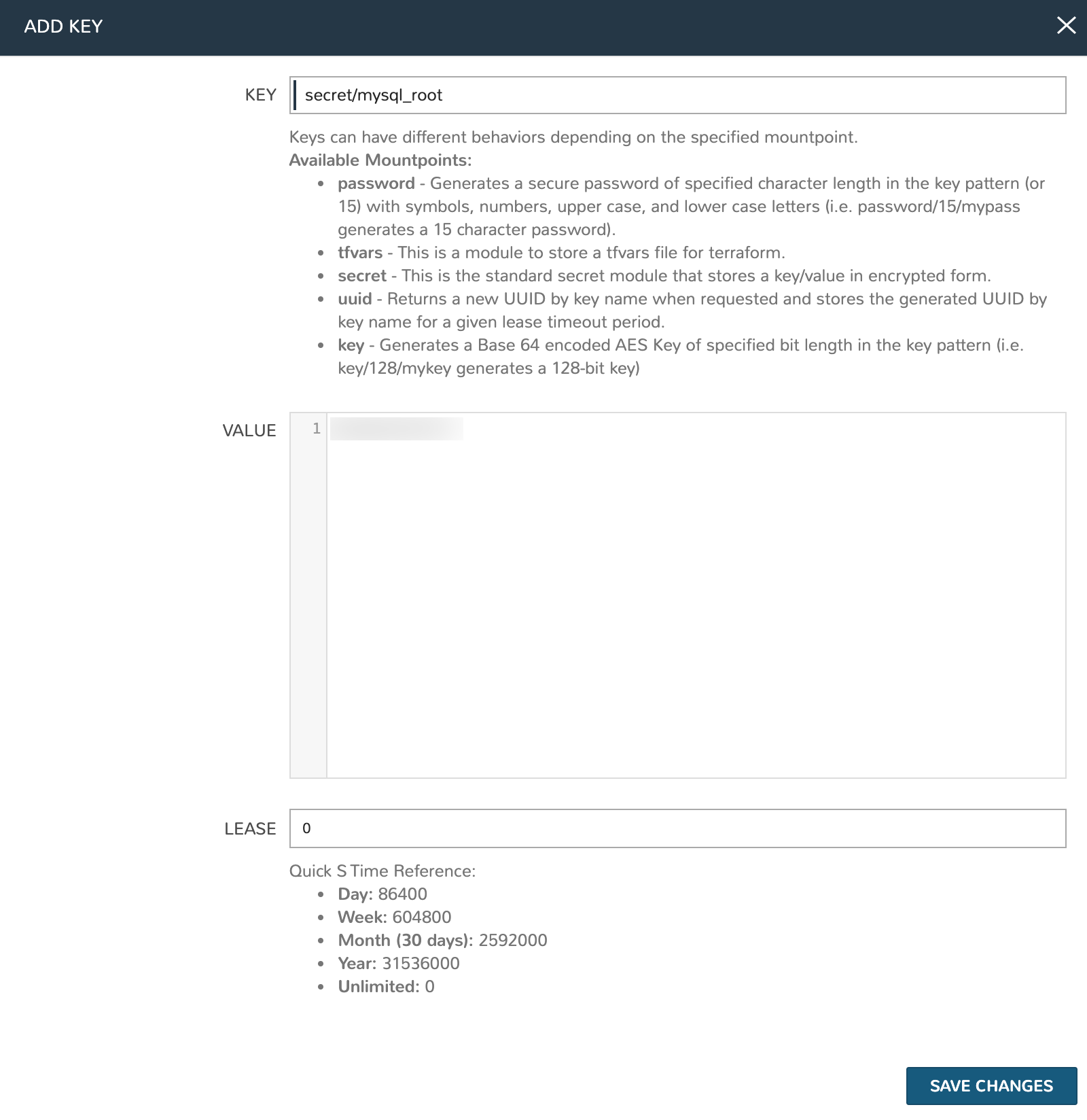
Once the plugin is added, we configure the connection details here. Edit the new Conjur plugin by clicking the pencil (✎) icon from its row in the list. Configure the following fields:
NAME: A friendly name for the new integration to identify it within HPE Morpheus Enterprise
ENABLED: Mark the box to make this integration active and available
CONJUR API URL: The full URL for the Conjur server, usually listening on port 8443
CONJUR USERNAME: The Conjur user account you wish to authenticate with. This user should have read, write, and execute access to the variables configured within the Conjur policy
CONJUR USERNAME API KEY: The API key for user entered in the prior field
CONJUR ORGANIZATION: The Conjur account in which the user and variables reside
CLEAR SECRET ON DELETION: When marked, secret values will be cleared when deleted from HPE Morpheus Enterprise
Important
Variables are predefined by Conjur policies. This integration does not allow users to create variables but does allow you to read and update their values. If the plugin is configured to clear secrets that are deleted from HPE Morpheus Enterprise, the variable value is updated with an empty value as there is no concept of fully deleting secrets in the Conjur API. If the plugin is configured not to clear secrets on deletion, the secret object is deleted from HPE Morpheus Enterprise without altering it on the Conjur backend.
By applying and configuring the plugin, the appliance now has the Conjur/Cypher integration available. If you don’t intend to use the credential store integration, you can stop here and look ahead to the feature demonstration further ahead in this guide. If you do intend to use the credential store integration as well, there’s one additional configuration step to take in the next section.
Adding A Conjur Trust Integration¶
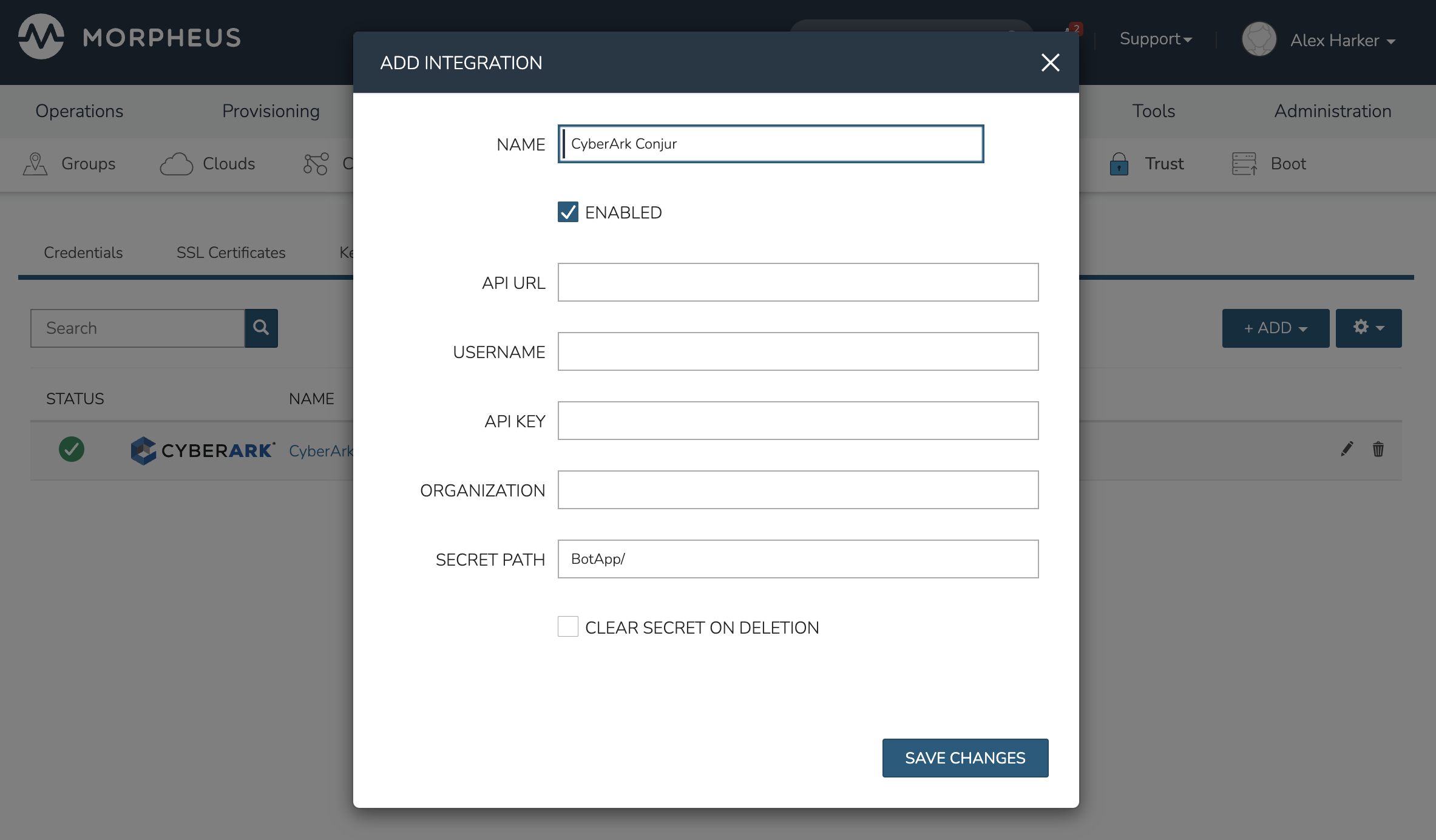
In order to use Conjur with HPE Morpheus Enterprise credentials, we must also add a Conjur-type integration in Infrastructure > Trust > Integrations. By applying the plugin in the previous step, we now have the ability to add this type of integration. From the Trust integrations list page, click + ADD and select “Conjur.” It’s important to note that you do not need to again configure the API URL and Conjur login credentials as we just did in the previous step. You may configure them here if you wish, such as if you were making multiple integrations with multiple Conjur appliances, but if you’re simply integrating with the same appliance and user account, this is unnecessary. Simply give the new Trust integration a friendly name for reference in HPE Morpheus Enterprise and indicate the desired mount point for secrets you wish to consume as done in the screenshot below.
Note
In many cases, you don’t have to configure the connection details when adding a Conjur Trust integration. See the paragraph above.
Conjur and Credential Stores¶
With configurations completed, we can take a look at how HPE Morpheus Enterprise is able to interface with Conjur as a credential store. As mentioned at the beginning of this guide, variables are created by Conjur policies and not by HPE Morpheus Enterprise. We can reference existing variables and update the secret values stored within.
As an example, there is a variable named BotApp/secretVar in the target Conjur appliance. When configuring the Trust integration (in the prior section), the BotApp/ mount point was referenced (see the screenshot in the last section). When creating stored credential sets in HPE Morpheus Enterprise against this Conjur credential store, reference the rest of the variable path as the NAME value on the credential set. In this case, the credential set will be named secretVar to complete the BotApp/secretVar path as shown in the screenshot below. Be sure to also select Conjur as the CREDENTIAL STORE value rather than the default “Internal.”
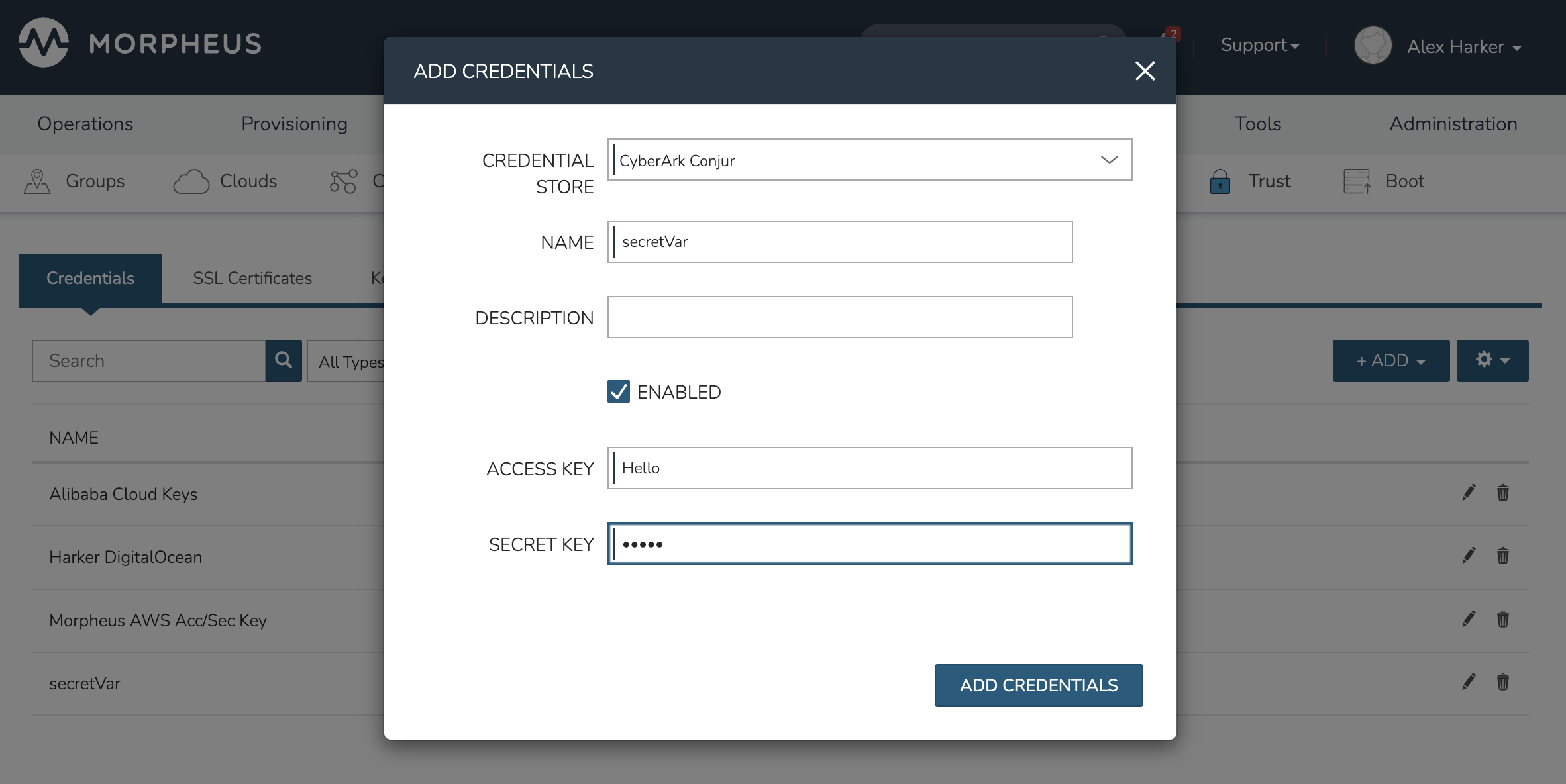
After saving and going back to the Conjur appliance, the value stored at the referenced variable has been updated. This credential set is also available for use anywhere HPE Morpheus Enterprise allows users to utilize them, such as when integrating new Clouds, authenticating REST calls to populate Option Lists, and many other places.
Conjur and Cypher¶
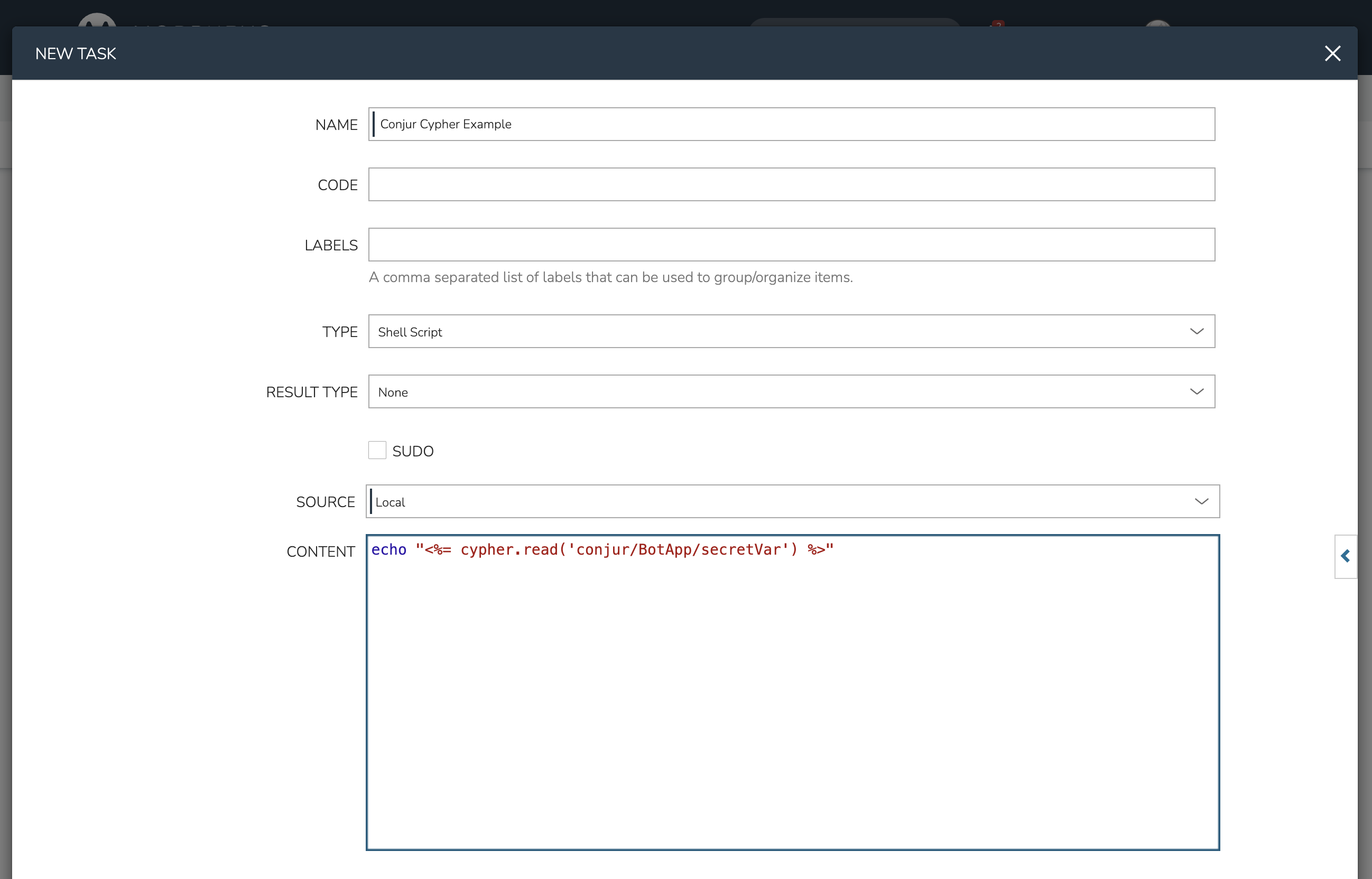
In addition to stored credential sets, the CyberArk Conjur plugin also enables integration with HPE Morpheus Enterprise Cypher. Just as calls can be made to internally-stored secret values with Cypher, Conjur variable endpoints may be referenced to onboard secret strings into automation Tasks.
In the screenshot below, see a simple shell script Task which echoes out a secret value stored in Conjur. As you can see, the conjur/ mount point is referenced along with the rest of the path to the variable which should be accessed. After executing the Task, we can check the execution history and see that the Conjur-stored value is indeed echoed back out.
If desired, the value stored in Conjur could also be updated through the HPE Morpheus Enterprise Cypher UI. Navigate to Tools > Cypher and click + ADD. Note the conjur mount point is included in the example list of available mount points shown in the modal. By creating a new Cypher entry at the conjur mount point which references an existing Conjur variable path, the value in Conjur can be overwritten. If you’ve configured the plugin to clear secrets on deletion, you can also update the stored value with an empty string when you delete the Cypher object in HPE Morpheus Enterprise. For our example case, we could update the value in Conjur by creating a Cypher entry at the mount point conjur/BotApp/secretVar.